Today’s hot topic is password best practices. As of July 2020 the internet had close to 4.57 Billion active users. Yes, most the of earth’s population at the time. The vast majority of this digital population, if not all, have to manage one or more sets of credentials. That is, a username and a password. Be it for social media accounts, email, banking, and the list goes on. In fact, the average internet user, new research suggests, has to manage an astonishing 70-80 passwords. We could do the math, but let us not digress from our hot topic of top 10 password best practices.
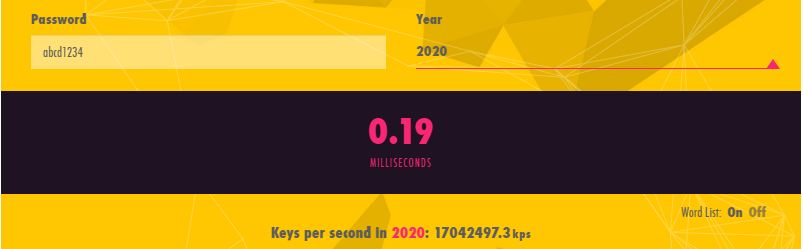
If only everyone would follow our top 10 password best practices, the internet would be a safer and more secure place. But let us admit, most of us do not. We religiously re-use our passwords across multiple sites, systems, and applications. According to a Google Security Survey, 52% of users re-use the same password for multiple accounts. Users also regularly elect insecure passwords like “iloveu” and “abcd1234”, which can be cracked in 0.19 milliseconds according to betterbuys.com Estimating Password Cracking Times tool.
For more mind boggling password statistics see idagent.com’s 10 Password Security Statistics.
Here are our top 10 password best practices to help protect your accounts.
Top 10 Password Best Practices
1. Use two-factor authentication
First and foremost, there is an inherent issue with passwords. Longer and more complex passwords are harder to remember, while shorter and simpler passwords are easier to crack (or guess). That is why regardless of a password’s length and complexity, the best line of defense against getting “hacked” is to compliment your passwords with two-factor authentication whenever possible. Two-factor authentication is an extra piece of information besides your username and password that only you know or have access to. So even if your password is compromised, the likelihood of someone else having your second-factor information is low.
2. Create a long and complex password
Use an online complex password generator such as makepwd.com or an offline generator such as KeePass’s password generation tool. According to betterbuys.com’s password cracking calculator, an 8-character non-complex password such as abcd1234 would take 0.19 milliseconds to crack using a brute-force atack method at 17042497.3kps (password keys attempted per second) while an 8-character complex password such as ‘4X!yfcW!’ would take approximately 9.5 years in the year 2020. A 12-character complex password such as ‘Y@tE!m@5BF8i’ would take 683638 millenia and 7 decades to crack using the same method. As a rule of thumb, and take this with a grain of salt, a long and complex password consists of at least 12 characters including uppercase and lowercase letters as well as numeric and special characters. Having said that, we would not use a 12-character password, no matter how complex, to protect against an accidental nuclear missile launch or to safeguard Coca-Cola’s secret formula recipe vault. If we are not mistaken they use two-factor authentication!
3. Avoid using dictionary words
Dictionary words in the CyberSecurity world are common letter (and/or number) combinations that can make up words such as ‘password’, ‘monkey’, ‘love’, ‘summer’ but can also include names such as ‘robert’, ‘george’, ‘yankees’, ‘jessica’ and other combinations such as ‘123456’, etc. Avoid using these in and of themselves because they are easily guessable and can lead to your passwords being cracked.
4. Use a different password for every account
This one is obvious. Use a different password for every site, system, or account in general. Consider this scenario. You create a FaceBook account “[email protected]” with password “J&dP3j3snaGd!PaD!bEB#@Pw5z5+eYLZ”, which is fairly complex but it also happens to be your email password for that email address. Well, you have just opened yourself up to anyone with backend access to Facebook systems to knowing your email credentials. Not that FaceBook stores passwords in a non-hashed way and not that they would EVER use this information to hack your email account, but how about those other smaller, less trustworthy anonymous websites you sign up with?
5. Avoid using the “Remember my password” option
There are 2 reasons to avoid the “Remember my password” option in browsers and other applications. First and foremost is if the “bad guys” gain access to your device, then they have automatically just gained access to every other saved credential on that device. Second reason to avoid the “Remember my password” option is those saved passwords can, in some cases, easily be revealed depending on how they are encrypted by the application.
6. Always log in via an encrypted connection
For websites, always make sure that the sign-in page is HTTPS (not HTTP) and is using a valid SSL certificate to secure the traffic. An HTTPS page ensures that the information exchange between the client (i.e. your browser) and the server is not readable if intercepted on the network. Look for the lock icon beside the URL field in your browser.
7. Keep your passwords to yourself
Never ever give out your passwords. To anyone. No exceptions. As an alternative, consider delegating access instead where possible.
8. Use a password management solution
Use a password management solution to store your passwords. Realize that ‘cloud’ password management solutions can have their own drawbacks (i.e. security, availability). This is a matter of opinion, but we like to store passwords offline or “onpremises” using password management solutions such as KeePass for personal credentials and CyberArk in the corporate world, but this is a matter of preference. Do your research before entrusting your password vault to a third-party.
9. Be proactive
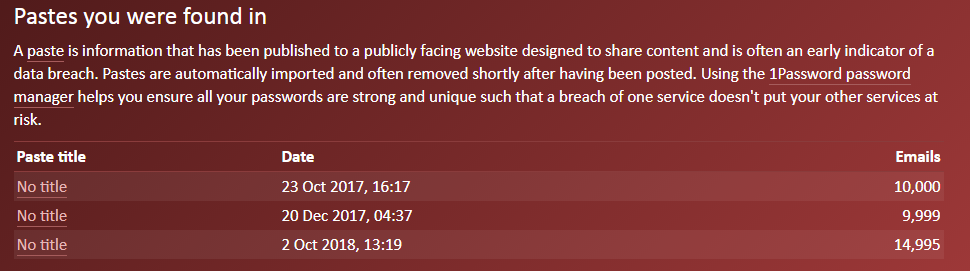
Be proactive and check websites such as Troy Hunt’s haveibeenpwned.com to see if you have any accounts that have been compromised in a data breach. Immediately change your password if you have reason to suspect your account may have been compromised.
10. See Best Practice #1
Passwords are as static as how often they are not changed. Use two-factor authentication whenever possible.